Chaos Labs Asset Protection Tool
DeFi protocols discover attack surfaces only after they have been exploited. With the recent decrease in market prices and liquidity, manipulation is an increasing concern for asset support. Chaos is unveiling a new tool to measure manipulation risk and protect against it.
Background
Protocols are constantly looking to expand asset support. A diverse asset offering appeals to a broader community and drives higher protocol usage and revenues.
However, there are challenges and risks associated with new asset listings. When considering new assets, it is crucial to consider how vulnerable it is to manipulation by adversarial actors. For example, let’s consider a borrowing protocol, supporting a new asset. A trivial attack vector is:
- Providing an asset with thin liquidity as collateral
- Pumping the asset’s price on relevant platforms (aka “oracle manipulation”)
- Draining the protocol of high-quality assets (think WETH, WBTC, etc.) by increasing your borrow against the newly priced pumped collateral.
Once the attack is over, the pumped price will drop, and the loss will likely turn into protocol bad debt as liquidators will not be able to react quickly enough.
Across the DeFi ecosystem, previous discussions around this type of vulnerability have been qualitative rather than quantitative, often leading to fluid “judgment calls.” With the recent market downturn, many previously high-quality collateral assets present a real risk to protocols due to depressed volume and valuations. While communities should clearly delist some assets, others carry a less decisive risk-reward profile. The challenge is understanding under what circumstances and parameters it would be safe to deploy a given asset as collateral. The Mango squeeze was a high-profile manipulation and highlighted the growing urgency of this attack vector.
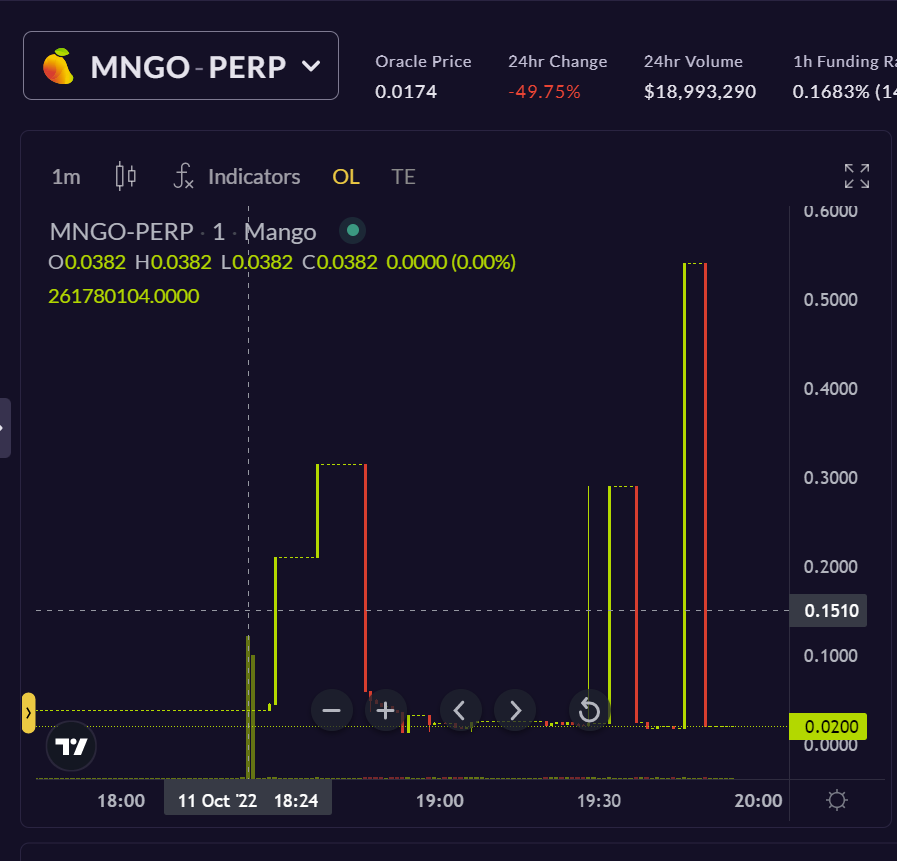
* Attacker Moving Mango Spot Prices *
Due to the constant threat of this attack, we have built a framework and monitoring tool to quantify the risk posed to our customers by identifying vulnerable assets and illustrating the appropriate protective measures.
Market Manipulation vs. Oracle Manipulation
In the past, protocols relied on inefficient oracles that could be manipulated at a relatively low cost compared with the price required to move the asset price across all markets. Today this is the exception to the rule. Price feeds are a known attack vector, and the most prominent protocols source the data from multiple liquid data sources to increase reliability and increase the price of manipulation. Therefore, an attacker must spread purchasing capital across several major exchange venues to manipulate the asset price. Throughout the past year, this was usually a costly attack; however, if we consider that some major asset prices have dropped 70%+ and the liquidity in the markets has shrunk by 50%+, the attacks have become significantly more achievable.
Feasible attacks vs. Theoretical Attacks
To properly understand the feasibility of such attacks, we need to consider two significant factors:
- The cost to move the price of an asset significantly.
- The derived profit an attacker may get out of the attack.
Both are important. Consider a scenario where the cost of price manipulation is $1B, which would result in a $50m profit. Such a considerable manipulation cost would lower the population capable of such an attack. Additionally, for those who could gather the appropriate funds, one would expect a rational attacker to pursue an extremely high profit to handle the associated risks. $50M in profit, or 5%, would be a small return for anyone putting that much capital at risk to engineer the necessary market conditions.
Simulating the Attacks
At Chaos Labs, we have harnessed the power of both on-chain and off-chain simulations to simulate collateral asset attacks and evaluate their feasibility by considering both the cost of manipulation and ROI to the attacker.
Cost of Manipulation
The cost of manipulation can broadly be divided into two distinct components:
- Price pumping: In the first phase of the attack, a malicious actor will choose a venue to manipulate liquidity. On a CEX, this would require filling a significant part of the sell orders in the order book (i.e., buying the “asks”) to set a new price. On an AMM-based DEX, this would require swaps to move the price to the attacker's target.
- Defending the new price: Once the attacker drives up the price, they will need to defend it for the duration of the attack - until they can borrow more from the protocol and solidify their gains. A large spike in price will lead to arbitrageurs selling into the market, which the attacker will need to buy to maintain the target price.
Analyzing Attacker Profit
Assuming rational actors and access to capital, the likelihood of an attack is a function of the expected profit. Of course, this attack carries risk for the attacker who needs to secure and spend significant capital upfront before realizing returns.
For example, they will need to determine much it will cost and how much they are willing to commit, to defend the newly set price. This depends on which actors and arbitragers will react fast enough to real-time market changes. Therefore, it stands to reason that a rational actor should only execute such an attack if the return on initial capital is significant and justifies the downside risk. A basic attack would analyze the profit as a function of collateral supplied and borrows against the newly pumped price. However, there are other strategies that the attack can initiate to hedge risk, such as shorting tokens affected by such an attack.
We believe transparency is crucial, and we do share our work in depth. However, we have decided not to disclose the complete methodology. This attack is high risk for a malicious actor and requires a very nuanced understanding of centralized, decentralized markets, market maker behavior, and much more. An in-depth guide could provide Blackhats with a framework to estimate attack costs and anticipate optimal market conditions before executing and draining target protocols. If you’re a protocol or company and this is interesting, of course, feel free to reach out to discuss.
Real-world example
Following the Mango squeeze, we utilized our system to run a simulation of an asset price manipulation attack (as a safety precaution, we will use a fake asset, ImaginaryCoin ($IMC) for the manipulated asset and not disclose the protocol name in this example).
Historically, ImaginaryCoin had relatively high liquidity in the market with daily trading volumes in the $10Ms. However, liquidity dropped significantly in the weeks prior to our simulation.
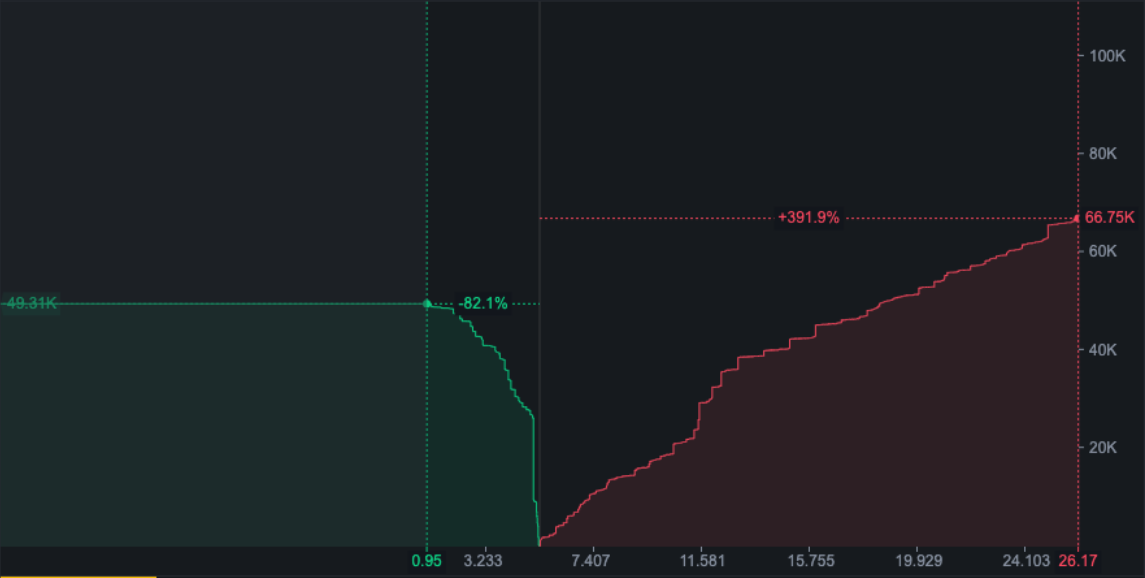
* The most liquid pair IMC/USDT from a major exchange’s order book depth shows that the sell side in total is significantly below $1M. Dated the first week of November. *
Our analysis showed that if the asset were listed as collateral on the protocol with the original risk parameters configured, the protocol would be highly vulnerable to a well-funded attacker.
We can confidently determine that if an attacker chose a time when markets are most susceptible to manipulation due to relatively depressed volumes, a profitable and feasible attack could have been launched with initial capital well below $100M. If the attacker was willing to deploy $250M, such an attack was almost inevitable under the said market conditions, even under the most adverse conditions for the attacker.
* This is an example of a target protocol configuration. This can be uniquely configured for any protocol. *
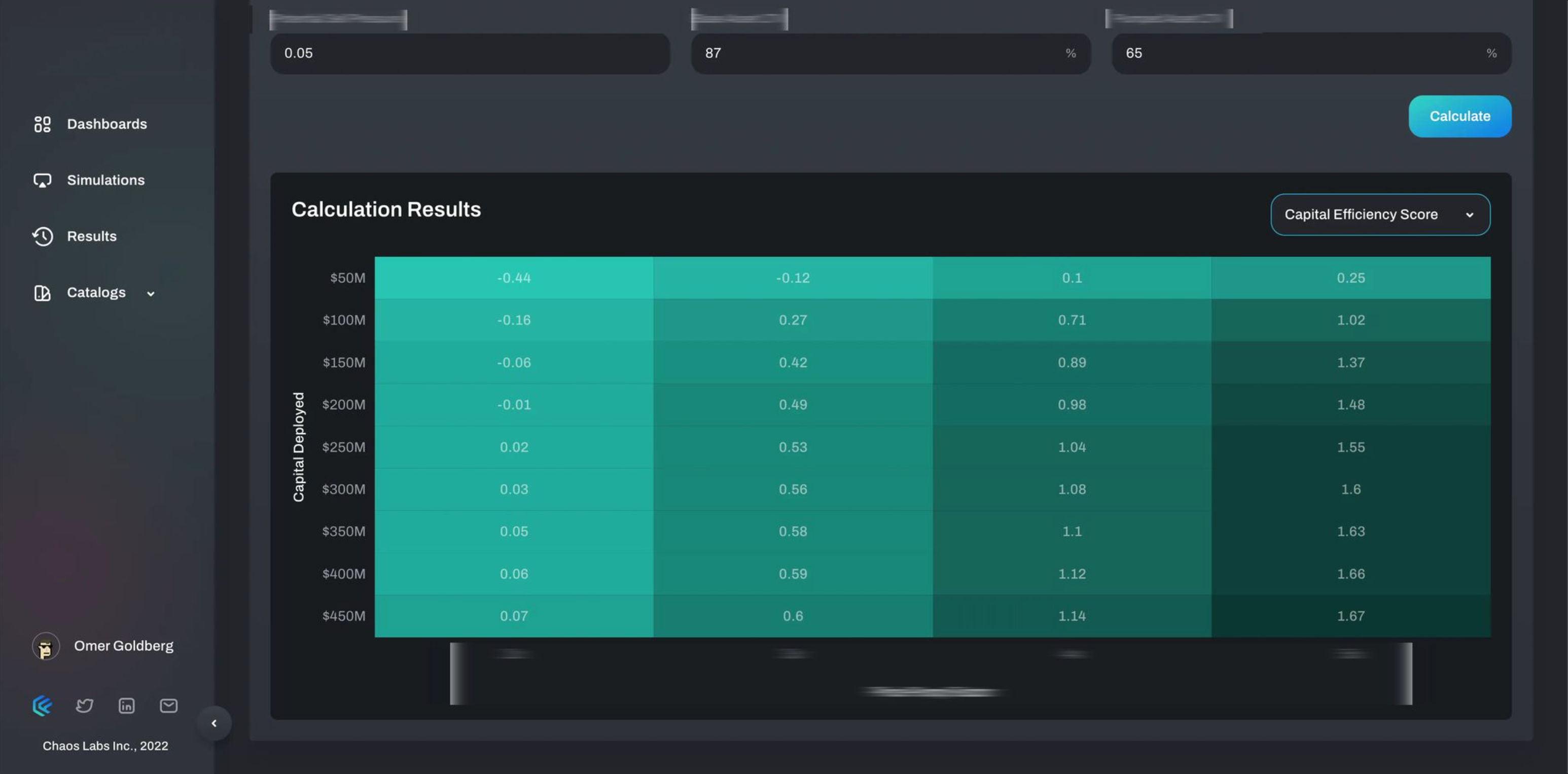
* This is an example of a partial analysis of possible attacks on ImaginaryCoin on the protocol. The results matrix displays the capital efficiency of such an attack as a function of capital deployed by the attacker. *
Playing safe doesn’t mean giving up
Once we have a way to determine an attack's cost and profitability, we can derive the risk parameters that will make such an attack unreasonable. As we have mentioned earlier, deeming assets as “risky” is easy, but then we give up on listing new assets that can increase community engagement and protocol usage. Naturally, adjusting the Loan-to-Value and Liquidation Thresholds of assets to minimal figures will be safe but will erode any revenue opportunities for the protocol. The Asset Protection Tool's value is finding the configurations that maximize protocol borrow usage while keeping it safe from such exploits.
For example, let’s consider the following:
- An attacker needs $150M to pump an asset price 5x
- The LTV of the collateral asset is 70%
If the attacker supplies $100M worth of the collateral asset and borrows $70m, then the attacker will need another $80M to complete the attack totaling $180M. For this example, we can assume that the attacker won’t be able to withdraw the initial $100 million supplied to the protocol, and it will become bad debt. Therefore, the amount borrowed post-manipulation and retained by the attacker is $100M x 0.7 x 4 = $280M. $100M profit for a $180M upfront cost, a 55% return, is potentially attractive.
However, suppose we change the LTV to 50%. In that case, we can likely avoid the attack because then, with $100M supplied as collateral, the attacker will need another $100M to complete the attack, and the payoff will be $100M x 0.5 x 4 = $200M leaving the attacker with zero profit.
For protocols with more dynamic risk parameters and advanced risk mitigation mechanisms, the flexibility is even greater. For example, AAVE introduces supply caps in V3, for which we will soon be able to recommend specific LTV, Liquidation Threshold, and Supply Caps that will make the listing of assets to the protocol even safer.
We do this by running simulations of different price trajectories and changes to asset liquidity that allow us to derive the feasibility of such attacks under various market conditions.
What's Next
The Asset Protection Tool is critical in determining protocol risk and vulnerability to specific attack vectors. It will serve as an effective “white hat” tool to protect DeFi protocols and be utilized by Chaos and protocol core teams to stay a step ahead.
Alongside Chaos Labs’ novel, cloud-based, agent- and scenario-based simulation platform, the tool will provide valuable analysis and insight to support risk parameter recommendations and onboarding of new assets across different protocols.
If you want to learn how this new product can help protect your protocol from unforeseen attacks, please reach out!
Chaos Risk Dashboard Launches Live Alerts for Real-Time Risk Management
Chaos Risk Dashboard has rolled out new functionality that provides real-time alerts covering crucial indicators on the Aave v3 Risk Dashboard and BENQI Risk Dashboard.
Chaos Labs Dives Deep Into AAVE v3 Data Validity
Chaos Labs, a cloud security platform for DeFi applications, has discovered
Risk Less.
Know More.
Get priority access to the most powerful financial intelligence tool on the market.